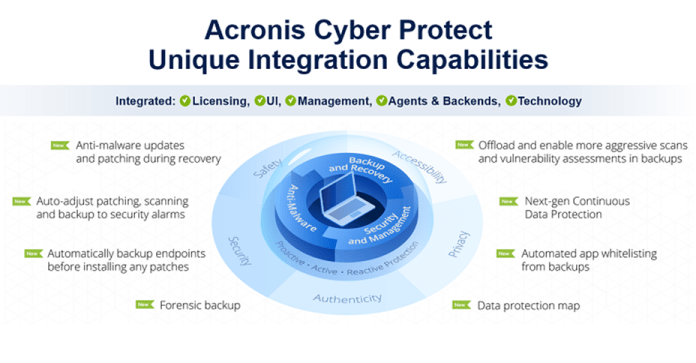
Acronis Cyber Protect is a cybersecurity solution that is designed for modern enterprises. It provides a customized and integrated solution to effectively manage digital threats.
Acronis Cyber Protect can deliver advanced cybersecurity to any endpoint device, whether it is remote, mobile, or onsite. In this article, we will discuss modern enterprise cybersecurity and how businesses can simplify their security by using enterprise endpoint protection strategies.
Acronis Cyber Protect is an integrated and customized solution for any modern enterprise where no one compromises on digital threats.
Acronis Cyber Protect provides easy and highly effective enterprise cybersecurity managed by one console, eliminates performance and compatibility issues and saves time and hassle associated with managing multiple tools.
Acronis Cyber Protect can also deliver advanced cybersecurity to any endpoint device irrespective of any location to match today’s remote, mobile or onsite work environment.
Acronis protection minimizes the complexity challenges of enterprise cybersecurity with industry proven data protection.
Investing and integrating with Acronis Protection for a cost effective Enterprise Cybersecurity can save time and give complete protection from modern day threats.
What is Enterprise Cybersecurity?
This Enterprise cybersecurity is designed to digitally safeguard assets and information to prevent cyber threats from anywhere.
By simplifying their cyber security technology stacks, organizations can reduce risk, improve cost efficiency and minimize cyber security failure.
An enterprise endpoint protection solution like Acronis protection that emphasizes manageable simplicity not only saves time and effort, but also greatly reduces the risk of data theft and cyber attacks.
The data can include anything from the organization’s website and online presence to its internal networks and data.
In order to ensure enterprise cybersecurity and provide enterprise endpoint protection to the organization, one must have a comprehensive cybersecurity strategy in place.
This includes using firewalls, antivirus software, encryption and other security measures like the Acronis protection to protect data from malicious actors.
It also involves educating employees on best practices for data security, such as using strong passwords and avoiding suspicious links.
Additionally, enterprise cybersecurity involves regularly monitoring networks for suspicious activity and responding quickly to any potential threats.
Enterprise cybersecurity also include the cloud, the Internet of Things, user identity verification, vendor or third party security, and anything else involved in end-to-end use.
The proper handling, storing and management of data are integral in data privacy to determine the enterprise endpoint protection required for each aspect.
This is important to ensure the proper application of solutions where advanced features can be used for better enterprise cybersecurity.
As global technology leaders evolve towards digital and analytics transformation, they are looking for simpler solutions with fewer complications in enterprise cybersecurity like Acronis Protection. They become anxious and seek options to keep all vulnerabilities at bay.
It is important to create effective business strategies for preventing and addressing cyberattacks. Modern digitally managed companies can streamline their security measures by implementing the following enterprise endpoint protection strategies:
1. Implement a comprehensive enterprise cybersecurity policy
Establish a comprehensive security policy that outlines the enterprise endpoint protection measures that must be taken to protect the enterprise’s data and systems.
2. Utilise strong authentication
Implement strong authentication methods such as multi-factor authentication to ensure that only authorized users can access the enterprise’s systems.
3. Firewall
As firewalls have always been defensive in network security, firewalls can be used to block malicious traffic from entering the network, as well as to monitor and control the traffic that is allowed to enter.
Firewalls can also be used to detect and prevent unauthorised access to the network. Installing a firewall to protect the enterprise’s network from external threatscan prevent an attack.
4. Monitor network traffic
For any suspicious activity, continue monitoring of network traffic and take appropriate action when necessary.
5. Encryption Implementation
On all data stored on the company’s systems, implementation of encryption protects against unauthorized access.
6. Regularly update software
To ensure that the latest security patches are applied, regular updating of the devices and software can protect enterprises from cyber threat.
7. Educate employees
User awareness training sessions to educate employees on the importance of enterprise cybersecurity and the measures they should take to protect the enterprise’s data and systems.
Enterprise Endpoint Protection
End points are where users interact with the network. Effective enterprise endpoint protection architecture includes the capabilities of a variety of endpoint security solutions.
As the volume and sophistication of cyber security threats has increased, the need for more advanced enterprise cybersecurity solutions for endpoints has increased.
Today’s enterprise endpoint protection systems like Acronis protection are designed to rapidly detect analyses, block and contain ongoing attacks.
Any company, whether small or large, should not neglect the cyber security of the company. An enterprise endpoint protection platform is a vital part of enterprise cybersecurity.
Some of the best practices can better protect a business by effective enterprise Endpoint Protection such as:
Threat identification and assessment, which involves research and analysis of the different types of threats that potentially affect an organization.
This includes researching the latest trends in cybercrime, understanding the different types of malware, and researching the different types of attack vectors that could be used against the organization.
Endpoint securities have taken a leap from the traditional antivirus software to a comprehensive enterprise endpoint protection sophisticated malware and evolving zero-day threats.
Enterprise environment contains a variety of endpoints like different versions of user devices, workstations, androids and tablets.
Executing strong authentication protocols such as two-factor authentication, multi-factor authentication, and biometric authentication.
Building and implementing a secured network and monitoring the flow of traffic while downloading or uploading documents during digital transit.
Integrating enterprise cybersecurity and enterprise endpoint protection solution with the organization’s infrastructure can upgrade the enterprise cybersecurity.
Such a mechanism helps in detecting the incoming threats on time and the security professionals can respond quickly.
Back up with unlimited endpoint protection along with patch management with regular software updates to fix the vulnerabilities on time. Acronis Cyber Protect eliminate gaps in defenses with integrated backup and anti-ransom ware technologies.
Conclusion
Enterprise security Protection management made easy with Acronis that features in safeguarding business with ransomware protection, quick and easy data backup and anti malware protection.
Enterprise endpoint protection solutions are designed to provide robust endpoint security at scale.
Acronis Protection gives an easy flexible deployment for any business any industry with most reliable and secure back up.
For exclusive offers and personalized offerings, get in touch with an Exabytes professional and plan Enterprise cyber security prevention of cyber attack, starting offer price per workstation starting S$6.25/license/mo and secure the enterprise environment.
Related articles: