Phishing emails are deceptive attempts to acquire sensitive information, such as passwords and credit card numbers. They appear to be from a reputable company, but they are actually from scammers attempting to deceive you.
If you fall victim to a phishing scam, the scammers can use your information to make fraudulent purchases, steal your identity, and more.
Fortunately, there are methods to recognise and avoid phishing attempts. Keep reading to learn how to avoid these scammers.
What is a Phish?
Understanding what a phishing email is is the first step to recognise one. The definition of a phishing email is an email sent with the ill intent of convincing the recipient to perform a specific action.
The perpetrator may employ social engineering techniques to make their email appear authentic and request sensitive information such as login credentials and passwords.
Socially Engineered Phishing Emails
Phishing emails with social engineering are the most dangerous. They are designed to be relevant to their objectives and appear authentic. The recipient is more receptive to the email and completes the specific task requested.
The outcomes may be catastrophic. If the recipient visits a malware-infected website, opens an attachment with a malicious payload, or discloses their login credentials, a scammer can gain unauthorised access to a corporate network.
How to Identify Phishing Emails
Oftentimes, phishing emails share common characteristics; they are frequently designed to elicit emotions such as curiosity, sympathy, dread, and greed.
If a team is informed of these characteristics and instructed on what to do when a threat is suspected, the time invested in training a team to recognise phishing emails can thwart a scammer’s attacks and network infiltration.
Knowing how to identify phishing emails will prevent you from becoming a victim.
1. Emails Demanding Immediate Action
Emails that threaten a negative consequence or opportunity loss unless immediate action is taken are frequently fraudulent.
This is a common tactic employed by scammers to induce recipients to act before they have had the opportunity to examine the email for potential defects or inconsistencies.
2. Emails with a Strange Greeting or Salutation
Emails sent between coworkers typically contain an informal greeting. Those that begin with “Dear” or contain phrases not typically used in informal conversation are likely from sources unfamiliar with the way of office interaction used by your company, and you should be suspicious of them.
3. Suspicious Attachments
The majority of work-related file sharing now occurs through collaboration platforms like Dropbox, OneDrive, etc.
Internal emails with attachments should always be viewed with suspicion, particularly if they have an unfamiliar extension or one commonly associated with malware (.exe, .zip, etc.).
4. Emails that ask for payment details, login credentials or other sensitive data
Emails originating from an unexpected or unfamiliar sender that request login credentials, payment information, or other sensitive data should be treated with extreme caution at all times.
Targeted phishers are able to forge login pages that resemble the real thing and send an email containing a link to the fake page.
Whenever a recipient is redirected to a login page or informed that a payment is due, they should not enter any information unless they are 100 percent certain that the email is genuine.
5. Inconsistency in Email Addresses, Domain Names and Links
Finding inconsistencies in email addresses, URLs, and domain names is another method for identifying phishing. Does the email originate from a frequently-corresponded-with organisation?
If so, compare the sender’s address to previous emails sent by the same company. Examine whether a link is valid by hovering the mouse pointer over it and observing what appears.
If an email claims to be from (for example) Microsoft but the domain name is different, it is a red flag.
6. Emails that are too good to be true
Emails that are too good to be true are those that encourage the recipient to click on a link or open an attachment by promising a reward of some kind.
If the sender is unknown or the recipient did not initiate contact, it is likely that this email is phishing-related.
Examples of these emails are those with email subjects, such as:
- You’ve won a lottery!
- Claim Your 1 Mil Prize Money!
- Winning Notification: Claim Your Prize
- Important Invoice Attached
The Notorious Domain Name Renewal Fraud
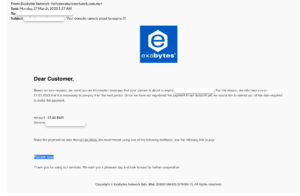
If you own a website or domain name, you should be aware of a new fraud scheme known as the ‘Domain Name Renewal Scam.’ Some of the examples of scam activity target on Exabytes:
Example 1:
Example 2:
Example 3:
This scam aims to convince people to transfer domain registration companies or ownership without their consent and/or to steal sensitive payment information from consumers.
This scam is especially convincing because it specifically mentions your domain name and attempts to pressure you into renewing it because it “will expire soon.”
You realise after a moment of consideration that your domain is, in fact, expiring shortly and on the exact date they specified.
How to Recognize and Avoid Domain Renewal Scams
Your initial reaction may be to panic and pay the balance immediately, but this can be fraud. Your contact information and domain registration details were likely obtained from a website such as WHOIS.
Here are some suggestions for avoiding these fraudulent scams:
- Ensure you are aware of your domain registrar’s name and only renew your domain name through the registrar’s official website.
- Avoid being coerced into paying ‘immediately’ for anything, particularly over the phone.
- Before paying for something that seems unusual, you should always read the fine print and conduct investigation. Professional phishers are now exceedingly adept at infiltrating all types of emails.
- Trust your intuition. If something doesn’t feel right, take the time to investigate and confirm its legitimacy.
| Reminder | Details |
|---|---|
| 1. | Appointing third party to pass the message |
| Details | Exabytes communicates with clients only through the following domains: exabytes.com, exabytes.my, exabytes.sg, exabytes.co.id, exabytes.cloud. No third party will be appointed to notify clients on behalf of Exabytes. |
| 2. | Fake Password Reset Notification |
| Details | Exabytes will not ask clients to log in to their mailbox/control panel or any login for security measurement/verification via system notification. |
| 3. | Fake Account Activation Verification |
| Details | Exabytes will not suspend hosting accounts without proper reason/procedure or ask clients to log in to unknown links for identity verification. |
Case Studies
As a web hosting provider and domain registrar with over 20 years of experience, Exabytes has discovered many phishing attempts that targeted our clients.
One such scam disguised the email content with the Exabytes logo and included Exabytes details in the signature.
Read more about these phishing attempts here, and learn how to avoid them here.
Final takeaways
It’s important to be extra careful and aware of phishing scams. By learning to spot the signs of a phishing email, like a suspicious sender or a weird-looking link, you can protect yourself from these sneaky scammers.
Remember to never give out your personal information, like passwords or credit card numbers, unless you’re sure it’s a trustworthy website. And always double check the sender and the link before clicking on anything.
Additionally, keep in mind that phishing scams can also happen over the phone.
Last but not least, legitimate companies, including banks, government agencies, and your domain registrar and web hosting provider, will never call you to ask for your passwords.
Related articles: